Table of Contents
In today’s interconnected digital world, safeguarding sensitive data and controlling who has access to what is of paramount importance. This is where Identity and Access Management (IAM) comes into play. IAM is a crucial component in the cybersecurity landscape, allowing organizations to manage digital identities and ensure that the right individuals have appropriate access to resources. Whether it’s employees, partners, or customers, IAM serves as the first line of defense in maintaining security while also supporting the user experience. For anyone interested in pursuing a career in cybersecurity or IT, understanding IAM is a fundamental skill.
What is IAM?
Identity and Access Management (IAM) refers to the processes, policies, and technologies that manage and secure identities in an IT environment. IAM ensures that users can only access the resources they are authorized to use. It is about managing digital identities, enforcing authentication methods, and controlling access permissions.
IAM solutions are designed to not only verify users’ identities but also govern what those users are allowed to do. Through well-implemented IAM policies, companies can maintain control over their critical data, minimize security breaches, and ensure compliance with industry standards.
Key Components of IAM
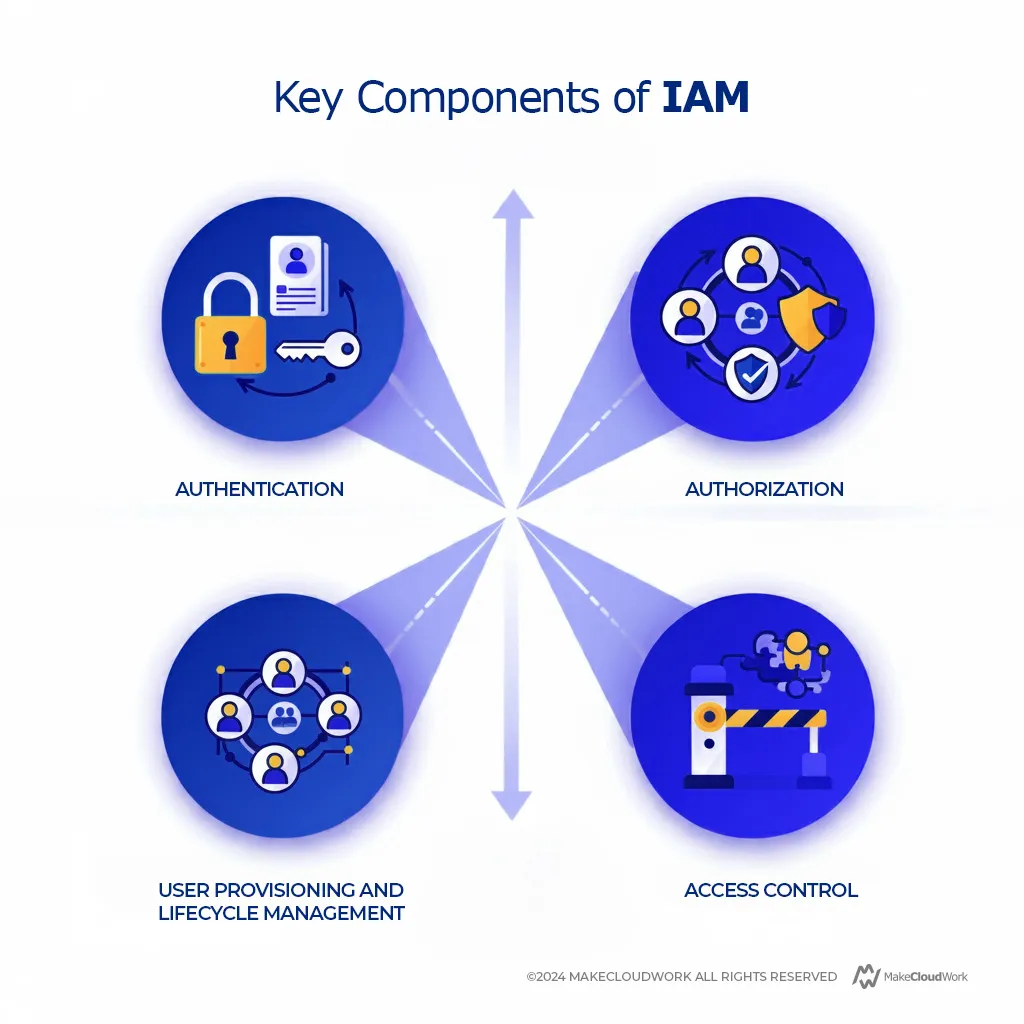
IAM solutions are typically built around a few key components:
- Authentication: Authentication ensures that users are who they claim to be. This process often involves something the user knows (e.g., a password), something they have (e.g., a smart card), or something they are (e.g., biometric data). Multi-Factor Authentication (MFA) is becoming a standard practice to enhance security.
- Authorization: Once a user is authenticated, authorization governs the level of access that user has. This means determining the data and applications a user can view or manipulate based on their role within the organization.
- User Provisioning and Lifecycle Management: IAM also involves creating, managing, and retiring user accounts. This process helps streamline onboarding and offboarding, ensuring that new hires get access to everything they need, while ex-employees lose access promptly upon leaving.
- Access Control: This is where IAM enforces security policies regarding who is allowed to do what within an organization’s digital ecosystem. Role-Based Access Control (RBAC) is commonly used, where permissions are assigned based on the user’s role within the company.
Benefits of Implementing IAM
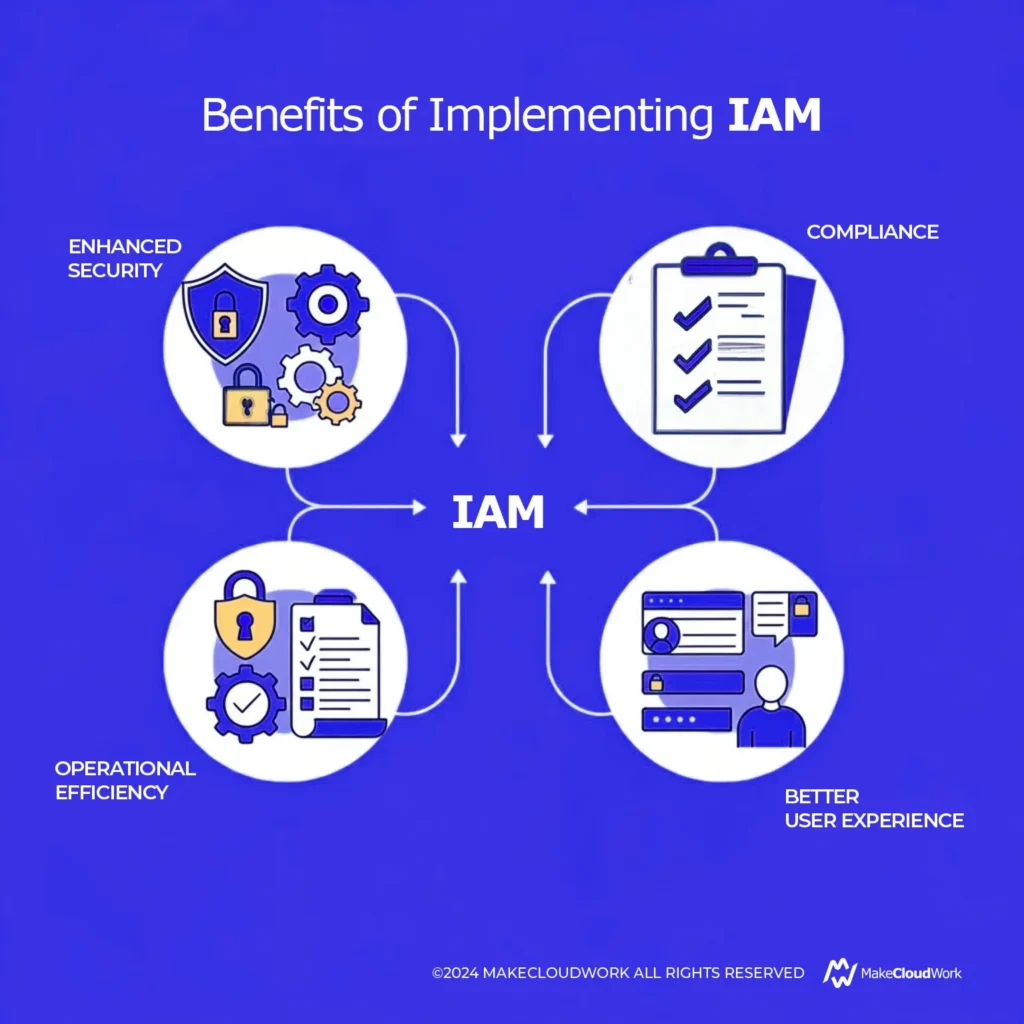
Properly implemented IAM systems offer several benefits for businesses:
- Enhanced Security: By enforcing strict identity verification and managing permissions carefully, IAM helps reduce the risk of unauthorized access, minimizing the chances of a data breach.
- Operational Efficiency: Automated IAM processes (such as provisioning and deprovisioning) help organizations reduce manual intervention, speeding up user access and minimizing human error.
- Compliance: Organizations must comply with various regulations that require them to manage access to sensitive information properly. IAM helps in demonstrating compliance with laws like GDPR, HIPAA, and more.
- Better User Experience: IAM can improve user experience by enabling Single Sign-On (SSO), which allows users to access multiple applications with a single set of credentials, making it more convenient for employees and customers alike.
Challenges in Implementing IAM
While IAM provides numerous benefits, implementing it is not without challenges. Organizations often face difficulties in integrating IAM with legacy systems, managing the complexities of user roles, and ensuring that IAM policies keep up with dynamic changes within the workforce. Moreover, IAM must be properly maintained to stay effective, which means keeping up with evolving threats and adapting the IAM framework as the organization grows.
IAM Training: A Critical Step in Security Preparedness
For businesses and IT professionals, understanding IAM goes beyond just knowing what it stands for. Practical training is essential to grasp the intricacies of setting up IAM frameworks, implementing proper user roles, and using IAM tools effectively. IAM training equips professionals with the skills needed to evaluate identity governance, assess risk, and implement IAM policies that align with business needs and compliance requirements.
IAM training programs typically cover key topics such as access control models, identity lifecycle management, authentication technologies, and hands-on experiences with popular IAM tools. By undergoing IAM training, IT professionals can better understand how to establish a secure and seamless access environment, ensuring business continuity and reducing vulnerability.
IAM Training for the Three Major Public Cloud Providers
When it comes to cloud environments, IAM plays a critical role in ensuring secure access to cloud resources. Each of the three major cloud providers—Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP)—offers distinct IAM services and tools. Understanding IAM in the context of these cloud platforms is essential for effectively managing cloud security.
- AWS Identity and Access Management: AWS IAM allows administrators to manage access to AWS services and resources securely. AWS IAM training focuses on concepts such as user roles, policies, permissions, and using IAM roles to control access across AWS accounts. Training also covers AWS services like AWS Organizations for managing multiple accounts, and how to implement least privilege access for securing the cloud environment.
- Azure Identity and Access Management: Microsoft Azure offers a robust IAM service through Azure Active Directory (Azure AD). Azure IAM training includes topics such as managing user identities, implementing role-based access control (RBAC), and setting up Conditional Access policies. Training programs also delve into using Azure AD for Single Sign-On (SSO), Multi-Factor Authentication (MFA), and managing Azure resources through service principals and managed identities.
- Google Cloud IAM: Google Cloud IAM helps organizations define and manage who can do what within their Google Cloud environment. Google Cloud IAM training emphasizes creating and managing roles, policies, and permissions to control access to resources. It also covers service accounts, managing access at both the project and resource levels, and ensuring compliance with security best practices within Google Cloud.
Training for these cloud platforms generally involves hands-on labs and practical exercises that simulate real-world scenarios. This helps learners to better understand the nuances of IAM implementation and ensures they are prepared to handle IAM tasks within a cloud environment. By focusing on IAM training for AWS, Azure, and GCP, professionals can gain a holistic understanding of identity management across different platforms, making them valuable assets for organizations operating in hybrid or multi-cloud environments.
How MakeCloudWork Can Help You Achieve IAM Expertise

MakeCloudWork is dedicated to helping professionals and organizations develop the skills needed to master IAM in both traditional and cloud-based environments. Our IAM training programs are tailored to meet the needs of different experience levels, from beginners to advanced practitioners. We provide:
Comprehensive Training Modules: MakeCloudWork offers foundational courses like IAM Essentials and advanced, in-depth programs like IAM Bootcamp. We cover IAM essentials, including authentication, authorization, and access control, with a focus on the three major public cloud providers—AWS, Azure, and Google Cloud. Our modules help learners understand both foundational and advanced IAM concepts, ensuring a deep understanding of identity governance and security best practices.
Hands-On Labs and Real-World Scenarios: Our training includes extensive hands-on labs that provide practical experience with IAM tools and services across AWS, Azure, and GCP. Learners work through real-world scenarios that simulate the challenges faced in managing identities and access in dynamic environments.
Customized Learning Paths: MakeCloudWork offers customized learning paths that align IAM training with specific organizational needs, ensuring that training is relevant and impactful. Whether your organization operates in a single cloud or a multi-cloud environment, we have the resources to tailor the learning experience to your requirements.
Expert-Led Training: Our courses are led by industry experts with extensive experience in cloud security and IAM. Learners benefit from the knowledge and guidance of professionals who have hands-on experience implementing IAM solutions in enterprise environments.
Support for Certification: MakeCloudWork also offers support for those looking to get certified in IAM for AWS, Azure, or Google Cloud. Our training programs are designed to help learners pass certification exams, equipping them with the skills and knowledge needed to achieve recognition in cloud IAM. Visit our IAM Certification page HERE for more information.
Whether you are an IT professional seeking to enhance your career prospects or an organization looking to upskill your workforce, MakeCloudWork can provide the tools and expertise needed to master IAM and ensure robust security in today’s digital landscape. Check out our IAM Course page HERE for more information.
Conclusion
Identity and Access Management is more than just a security measure—it’s a vital business enabler. As the need for secure data handling and access control grows, professionals who are skilled in IAM can provide immense value to organizations looking to protect their digital assets and ensure regulatory compliance. Incorporating comprehensive IAM training is an excellent way for organizations to develop these competencies in their teams, ultimately creating a safer and more efficient work environment.






